Table of Contents
Here is the factual data with no hype.
Latest benchmark: 16 February 2015 (raw data spreadsheet). (Previous: 2014-09-30, 2014-07-22)
This benchmark measures privacy exposure by counting the number of distinct 3rd-party domains hit by net requests. The lower the number of these 3rd-party domains, the better.
Some benchmarks measure the number of requests blocked, which I think is of no interest as a usable measurement of privacy exposure. The number of requests blocked is no guarantee of less distinct 3rd-party domains hit (and leaving a trace in the servers' logs).
My opinion is that the direct measurement of the number of distinct 3rd-party domains that get hit is much better and more relevant for privacy protection efficiency.
uBlock Origin (uBO) and Disconnect required no extra configuration steps. Other blockers required configuration. The one requiring the most for that benchmark was Adblock Plus (ABP).
Caveat: the definition of a "3rd-party" is a domain not matching the web page. Many domains reported as "3rd-party" actually belong to the same entity which owns the page domain (for example, yimg.com is owned by yahoo.com). There is no way for the benchmark code to know this unless using a comprehensive database of who owns which domain. That is beyond my means. Still, the benchmark is useful if comparing blockers among themselves or against when using no blocker.
The URLs (84) from the reference benchmark were used.
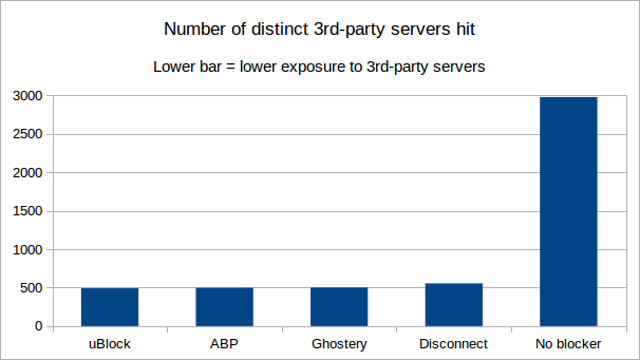
Results -- figures are "3rd party / all". Ordered from least 3rd-party hits to most 3rd-party hits. Privacy-wise, lower numbers are better.
uBO 0.8.8.1
- Distinct 1st-party/3rd-party pairs: 491
- Scripts: 980 / 1635
- Outbound cookies: 58 / 269
- Net requests: 3,987 / 7,956
ABP 1.8.10
- Distinct 1st-party/3rd-party pairs: 497
- Scripts: 1009 / 1733
- Outbound cookies: 67 / 284
- Net requests: 4,069 / 8,166
Ghostery 5.4.1
- Distinct 1st-party/3rd-party pairs: 501
- Scripts: 882 / 1619
- Outbound cookies: 120 / 370
- Net requests: 4,031 / 8,218
Disconnect 5.18.18
- Distinct 1st-party/3rd-party pairs: 555
- Scripts: 1186 / 1685
- Outbound cookies: 130 / 382
- Net requests: 4,462 / 8,219
No blocker
- Distinct 1st-party/3rd-party pairs: 2977
- Scripts: 3800 / 4647
- Outbound cookies: 1641 / 2097
- Net requests: 12,131 / 16,851
Notes
The figures show the number of requests allowed and lower numbers are better. The point is to count the number of distinct 3rd-party/1st-party pairs after running the reference benchmark (two repeats in the current instance).
The less distinct 3rd-party/1st-party pairs, the better.
Data diffs
These show the differences in what was not blocked. If something appears on side A but not on side B, it means side B has blocked something not blocked by side A and vice versa.
- uBO/ABP: https://www.diffchecker.com/czy6h5lq
- uBO/Ghostery: https://www.diffchecker.com/zapbh5b9
- uBO/Disconnect: https://www.diffchecker.com/386c367m
These diffs may help you decide whether you should complement uBO with another blocker, though remember you can always ask uBO to block more (dynamic filtering may come in handy for this).
Observations
Using the data diffs, one can observe that with uBO + default settings, there are large areas of privacy exposure related to:
facebook.net(45)facebook.com(44)googletagservices.com(39)twitter.com(34)taboola.com(11)
So if this concerns you (it should), I would say the best way to foil these is to use dynamic filtering. Here are the rules that will block all these 3rd-parties, except when used as 1st-party:
* facebook.com * block
* facebook.net * block
* googletagservices.com * block
* taboola.com * block
* twitter.com * block
facebook.com facebook.com * noop
facebook.com facebook.net * noop
twitter.com twitter.com * noop
With these few dynamic filtering rules, you would lower the "distinct 1st-party/3rd-party pairs" figure for uBO to 318 (down from 491). As a bonus, pages will load markedly faster.
You can unblock any blocked domains above for a specific site. For example, if ever you want Twitter widgets to work when visiting AnandTech, just set twitter.com to a local noop for that site, a mere point-and-click when using the dynamic filtering matrix.
Methodology
All blockers got configured in such a way as to compare apples to apples:
- Ghostery: Select all trackers except "Widgets". "GhostRank" unchecked. "Update now" clicked (and ensured that it used any new filters).
- uBO: Out-of-the-box settings -- no change.
- ABP: "EasyList" + "EasyPrivacy", "Peter Lowe's list", "Malware Domains" checked. "Acceptable ads" unchecked. "Update now" clicked.
- Disconnect: Out-of-the-box settings -- no change.
Browser settings (if you mind your privacy, there is no way around these settings):
- "Click to play" enabled.
I forgot to check "Block third-party cookies and site data", so 3rd-party cookies were allowed during the benchmark.
Sessbench performed the benchmarks. Each extension was tested alone, with no other extensions enabled in the browser.
The official Public Suffix List is used to determine the domain of a URL.
This file contains Unicode characters that might be confused with other characters. If you think that this is intentional, you can safely ignore this warning. Use the Escape button to reveal them.
- Wiki home
- About the Wiki documentation
- Permissions
- Privacy policy
- Info:
- The toolbar icon
- The popup user interface
- The context menu
- Dashboard
- Settings pane
- Filter lists pane
- My filters pane
- My rules pane
- Trusted sites pane
- Keyboard shortcuts
- The logger
- Element picker
- Element zapper
- Blocking mode
- Very easy mode
- Easy mode (default)
- Medium mode (optimal for advanced users)
- Hard mode
- Nightmare mode
- Strict blocking
- Few words about re-design of uBO's user interface
- Reference answers to various topics seen in the wild
- Overview of uBlock's network filtering engine
- Overview of uBlock's network filtering engine: details
- Does uBlock Origin block ads or just hide them?
- Doesn't uBlock Origin add overhead to page load?
- About "Why uBlock Origin works so much better than Pi‑hole does?"
- uBlock's blocking and protection effectiveness:
- uBlock's resource usage and efficiency:
- Memory footprint: what happens inside uBlock after installation
- uBlock vs. ABP: efficiency compared
- Counterpoint: Who cares about efficiency, I have 8 GB RAM and|or a quad core CPU
- Debunking "uBlock Origin is less efficient than Adguard" claims
- Myth: uBlock consumes over 80MB
- Myth: uBlock is just slightly less resource intensive than Adblock Plus
- Myth: uBlock consumes several or several dozen GB of RAM
- Various videos showing side by side comparison of the load speed of complex sites
- Own memory usage: benchmarks over time
- Contributed memory usage: benchmarks over time
- Can uBO crash a browser?
- Tools, tests
- Deploying uBlock Origin
- Proposal for integration/unit testing
- uBlock Origin Core (Node.js):
- Troubleshooting:
- Good external guides:
- Scientific papers
uBlock Origin - An efficient blocker for Chromium and Firefox. Fast and lean.